Following the “PrintNightmare” security vulnerability for the Windows Print Spooler Service and the subsequent KB applied by Microsoft, (see KB5005010: Restricting installation of new printer drivers after applying the July 6, 2021 updates), and updates released on August 10, 2021 or later have a default of 1 (enabled) for RestrictDriverInstallationToAdministrators.
As a consequence, the users get the following pop-up when trying to connect to their printers on print server: “Do you trust this printer?“.
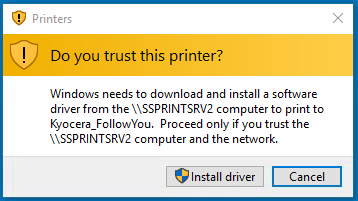
It is then required to elevate the process to install the printer driver “as Admin” (Install driver), when before, it was possible for the users to install the Point and Print drivers in their user sessions.
Since PrintNightmare it will be now necessary to configure different options to allow the users to map and install their Point and Print printer drivers dynamically in their session.
1) Configure Point and Print Restrictions (GPO)
- Open the group policy editor tool and go to Computer Configuration > Administrative Templates > Printers.
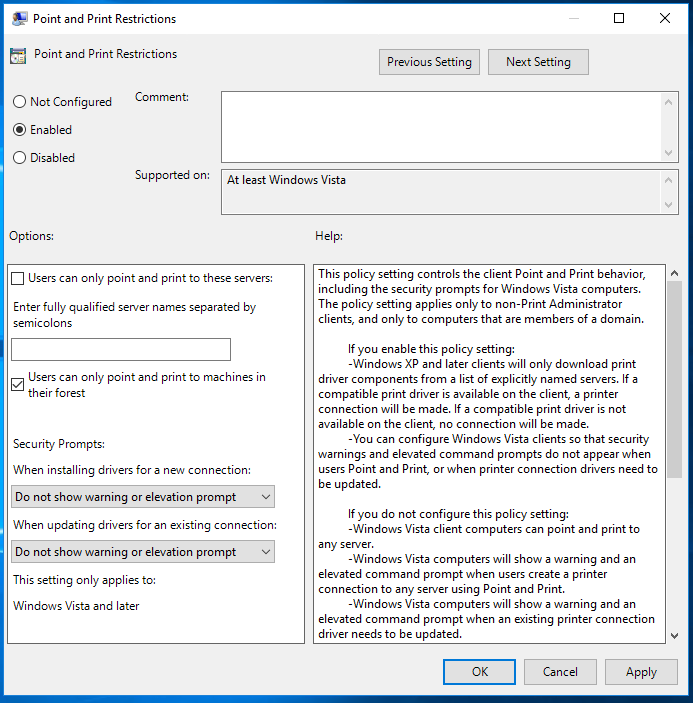
- Configure the Point and Print Restrictions Group Policy setting as follows:
- Policy is Enabled
- Check “User can only point and print to machines in their forest”
- When installing a driver (…) “Do not show warning or elevation prompt”
- When updating drivers (…) “Do not show warning or elevation prompt”
2) Configure Restrict Drivers Installation (for Printers)
- Open the group policy editor tool and go to Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options
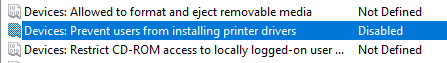
- Edit Devices: Prevent users from installing printer drivers and set it to Disabled.
3) Deploy registry key RestrictDriverInstallationToAdministrators (GPP)
Create a new registry parameter under the GPO section Computer Configuration > Preferences > Windows Settings > Registry.
- Action: Replace
- Hive: HKEY_LOCAL_MACHINE
- Key path: Software\Policies\Microsoft\Windows NT\Printers\PointAndPrint
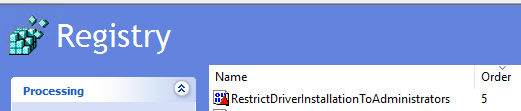
- Value name: RestrictDriverInstallationToAdministrators
- Value type: REG_DWORD
- Value data: 0
Run a “gpupdate” command on the machine as Adminstrator.
The security pop-up / warning and request for elevation for the Point and Print printers driver mapping will not be shown to the users.
