So many articles out there on setting up MFA for your vServers. I couldn’t find much on setting this up for the admin portion of ADC.
Part 1 deals with a simple configuration using ADC Radius, pointed to Duo for admin authentication and MFA.
In Part 2 I will deal with more complicated configurations using Microsoft NPS Server to do user roles in Radius for superuser vs lower command policy users.
MFA with Duo Authentication Proxy
Setup Duo Portal
Login to the Duo Administration Portal https://admin.duosecurity.com/login
Click “Applications”
Click “Protect an Application”
Click “Auth API” and select “Protect”

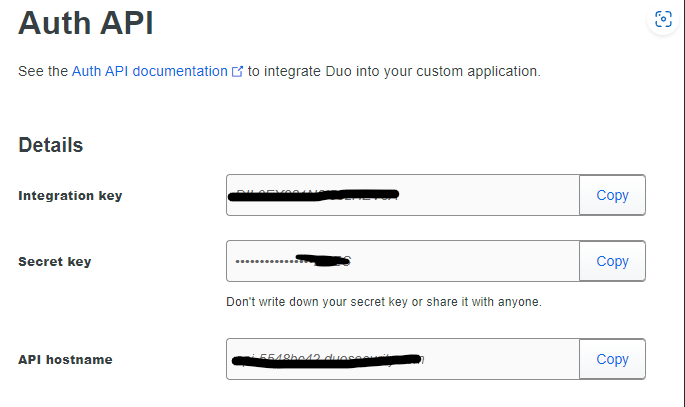
This will create an Integration Key, Secret Key, and API hostname. You will need these for the next step.
You can adjust the policies here if you need them. I would suggest turning everything off aside from PASSCODE authentication due to push-based attacks rampant now. I make a dedicated policy for Network Devices.
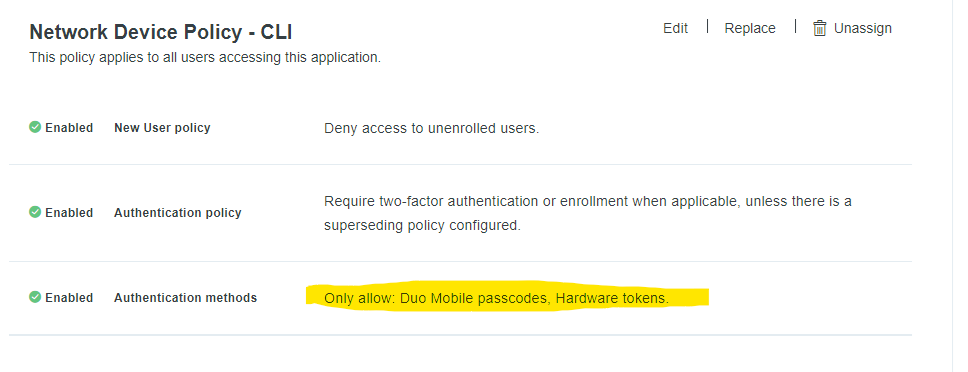
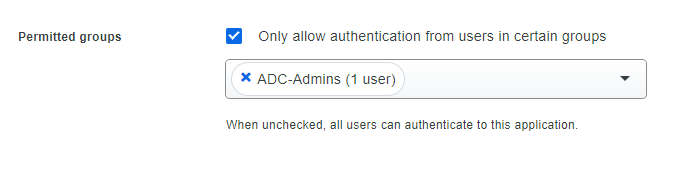
You also want to lock down this policy so only your ADC-Admins can authenticate to this application:
Install/Configure Duo Authentication Proxy
Download Duo Authentication Proxy from here. The website reference is here: Authentication Proxy Reference – Duo | Duo Security
It’s a pretty braindead install. Just install it and click next, next, next. It will open the configuration file for you. Or, you can just edit manually from C:\Program Files\Duo Security Authentication Proxy\conf\authproxy.cfg.
Here is an example cfg file:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
Here is an example cfg file: [radius_server_auto] ikey=XXXXXXXXXXXXXXXXXX skey=XXXXXXXXXXXXXXXXXX api_host=XXXXXXXXXXXXXX radius_ip_1=10.13.8.0/24 radius_secret_1=secret1 failmode=secure client=ad_client factors=auto factors=passcode port=18120 [ad_client] host=10.13.8.32 service_account_username=ldapbind service_account_password=Password123!! search_dn=OU=User Accounts,OU=Accounts,OU=LAB,DC=lab,DC=local |
Enter your Integration Key, Secret Key, and API hostname from the above Duo Portal steps in the ikey, skey, and api_host sections, respectively.
Under radius_ip_1, enter the subnet that your radius requests will be coming from. (Or just the IP of the ADC’s NSIP)
Under radius_secret_1 enter the radius secret that you will configure on your ADC.
I have hardcoded this config to ONLY allow passcode authentication with “factors=passcode”
ADC Setup
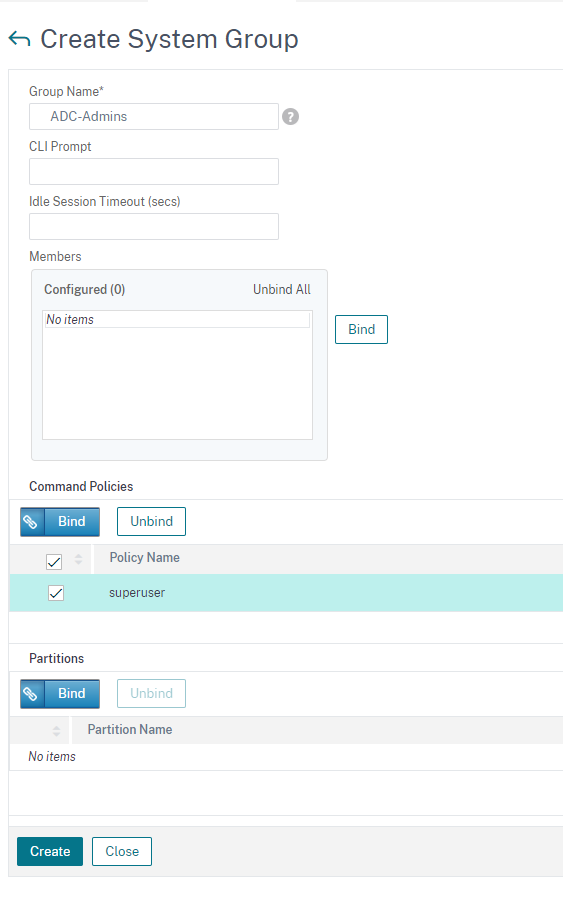
First, we need to setup a command group for Radius, so the users that can login get superuser rights (or really whatever rights you want them to have)
Go to System – User Administration – Groups – and hit “Add”. Set it up like the below (for superuser access) and click “Create”
Next, let’s configure the Radius server.
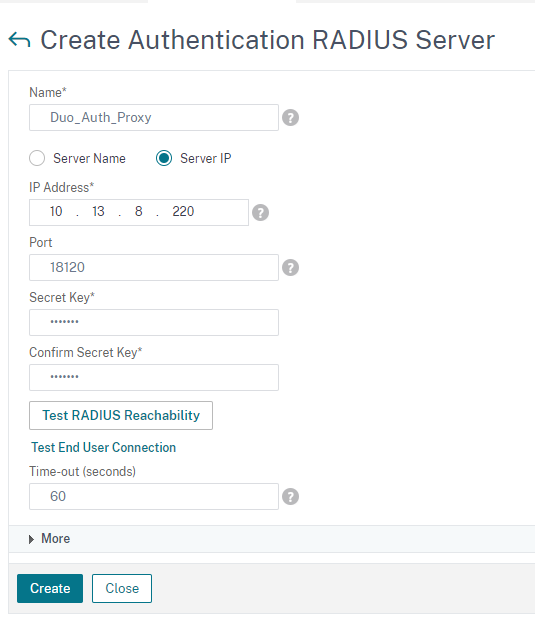
Go to System – Authentication – Basic Policies – RADIUS – Servers – and click “Add”
Set this up with the IP of your Duo Authentication Policy, the port and the secret you configured in the authproxy.cfg above, and set the Time-out to 60 seconds.
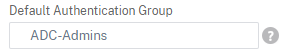
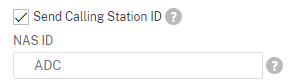
You will want to click “more” and set “Default Authentication Group” to ADC-Admins. I also like to hard-code a NAS-Identifier so I can use filters on Radius, if needed (This is needed if/when doing NPS Server)
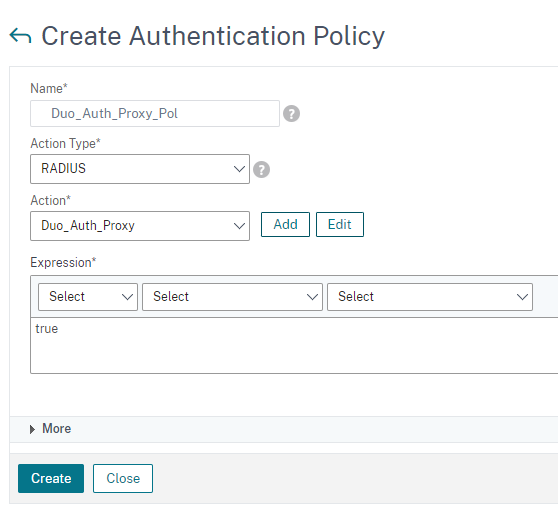
After saving this section, go to System – Authentication – Advanced Policies – Authentication Policies – and click “Add” and point it to your Radius Server above.
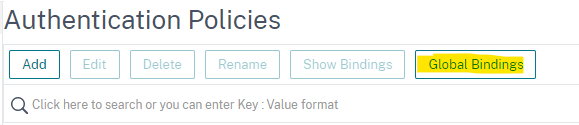
After you create this, you need to bind it globally. Click on “Global Bindings” in this same section.
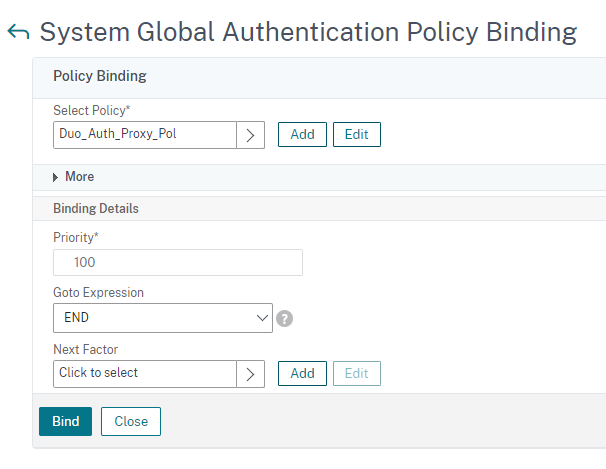
Set it up like this and click “bind” and click “done”
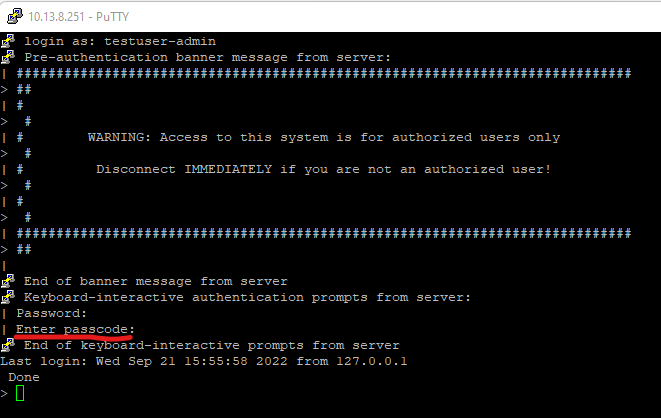
Now, let’s take a look at the authentication:
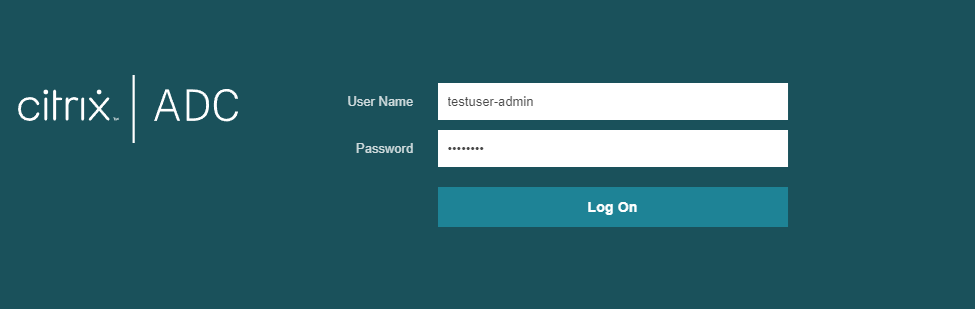
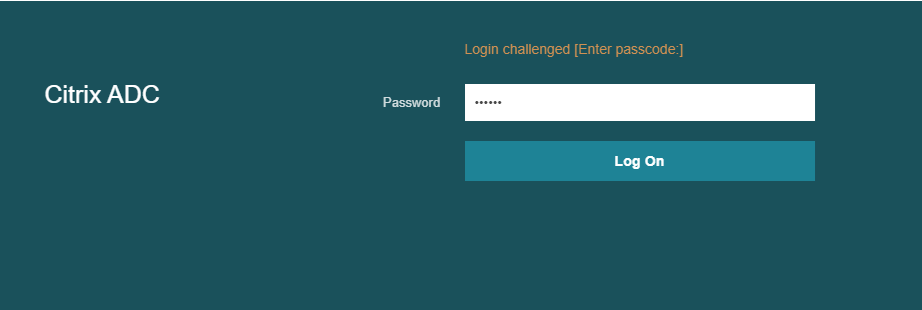
This also works the same for SSH.