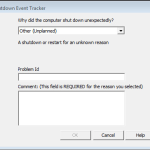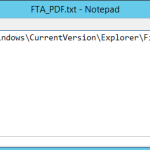
Thank you Microsoft for changing fundamental things about your operating system, with little or no regard to those of us running in an RDS/XenApp type environment. Check out this technet article. In this article it states how changes have been made. “In Pre-Win 8, apps could set the default handler for a file type/protocol by […]