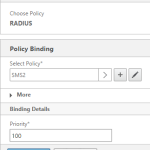
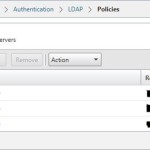
Part 1 here Synopsis In this example. We will be using Microsoft Network Policy Server (NPS) as the main Radius server. Using NPS we can setup 2 groups, which will allow us to setup read-only users (or whatever command group set you want) to login to ADC Admin portal without MFA, and forward any Admin […]